10 Cool New Cybersecurity Tools Announced At RSAC 2023
Top vendors including SentinelOne, Google Cloud and Cisco unveiled new products Monday to kick off RSA Conference 2023.

RSAC 2023 Is Here
RSA Conference 2023 officially kicked off Monday in San Francisco, and much has changed for the cybersecurity industry just since the last RSAC. The massive annual gathering at the Moscone Center most recently took place in June 2022, and while AI was certainly a major facet of the show at the time, that was still the “pre-ChatGPT” world. As RSAC 2023 gets underway this week, it will be more obvious than ever that the OpenAI chatbot has had a powerful impact on both cyber defense and attackers, setting off what many are calling an “arms race” around generative AI. This year, the flurry of RSAC-related product launches has already begun as of Monday, and generative AI technology is front-and-center in a number of them.
[Related: 15 New Cybersecurity Products To Know: Q1 2023]
The announcements so far have included generative AI-based offerings for security operations teams from companies including SentinelOne, Google Cloud and Accenture. The adoption of generative AI by these companies shows how the technology is already branching out in the cybersecurity industry beyond OpenAI and its GPT large language models.
There’s plenty going on outside of generative AI in the RSAC 2023 cybersecurity product announcements so far, as well. The hype around extended detection and response (XDR) at the conference is likely to be at least on par with last year, with vendors including Cisco debuting major new tools in the XDR segment. Several other security tools launched on the first day of RSAC also bring a focus on improved detection and response, as well as enhanced capabilities for security operations teams overall, including with IBM’s debut of a new suite of offerings for security analysts.
RSAC 2023 takes place this week from Monday, April 24, through Thursday, April 27.
What follows are the key details on 10 new cybersecurity tools announced so far at RSA Conference 2023.

SentinelOne Threat Hunting Tool
In what it’s calling a major advancement for security using generative AI, SentinelOne announced a new threat hunting tool for its Singularity platform that utilizes a large language model (LLM) in an effort to dramatically improve productivity for security analysts. SentinelOne is referring to the new generative AI-powered threat hunting tool as “Purple AI,” the company told CRN.
Analysts will be able to use the new generative AI interface in the Singularity Skylight platform to ask questions about threats in a customer’s environment — for instance, “is a certain threat actor present in this environment?” or “are there threat actors affiliated with China in my environment?” The ability to use natural language to query a system will offer massive time-savings to analysts and will allow security teams to respond to more alerts and catch more attacks, said Ric Smith, chief product and technology officer at SentinelOne.
The generative AI technology will also excel at providing analysts with summarizations of results, which “also alleviates some of the tedium around doing the actual analysis,” he said. As an example, analysts will be able to have the system tell them, “‘This is lateral movement. This is something that you should be aware of,’” Smith said.
Ultimately, a main goal of implementing generative AI technology in this way is around “making threat hunting more accessible,” he told CRN. With existing threat hunting platforms, “it’s pretty daunting [to use them]. You have to have a high level of skill to interact with these things,” Smith said. With the addition of this generative AI technology, however, SentinelOne believes the technology can now enable security operations center teams to scale up their threat-hunting activities, he said. “We think this will be a better method of general threat hunting.”
The large language model that’s helping to power the new threat hunting tool leverages both open-source and proprietary offerings in the space that are not being disclosed, Smith said. SentinelOne is also training the model on its own data and is doing “quite a bit of fine tuning” on the LLM to customize it for the security domain, he said.
The new SentinelOne threat hunting tool will initially be offered as an add-on to the Singularity Skylight platform, and is now in limited preview. Details about wider availability are not being released yet.
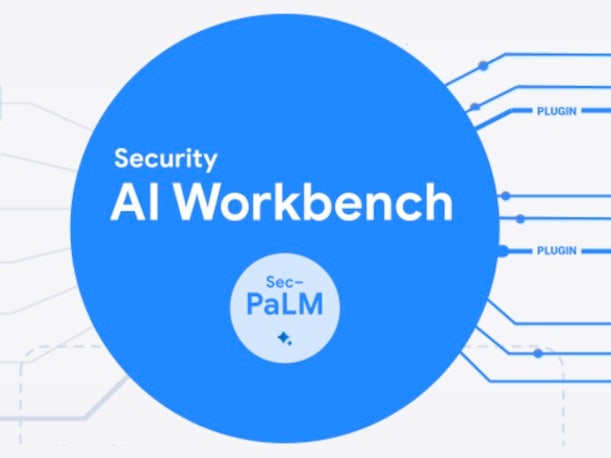
Google Cloud Security AI Workbench
In another big generative AI move in cybersecurity, Google Cloud unveiled its Security AI Workbench offering that’s powered by a new, security specific large language model known as Sec-PaLM. The model utilizes Google Cloud’s security intelligence via Google’s broad visibility into threat data and Mandiant’s esteemed threat intel around vulnerabilities and malware, as well as threat actors and threat indicators, according to Google Cloud.
“We have a unique opportunity in Google where we actually have both the infrastructure to cost-effectively deliver next-generation AI, but also to infuse it with threat intel, and a lot of data to train our own large language model,” said Sunil Potti, vice president and general manager for Google Cloud’s security business. “So rather than just say we’re using a Google version of the large language model, we’ve actually built a new security LLM.” While Sec-PaLM is based on Google’s LLM, “it’s customized and purpose-built — custom trained — using security-related data coming from all of our sources that we have currently,” Potti told CRN.
The Google Cloud Security AI Workbench is aimed at helping to reduce the overload from threat data and the large number of security tools in use, the company said. Customers will be able to provide their private data to the Security AI Workbench platform only at inference time to enhance privacy, Google Cloud said.
The first place Google Cloud will be implementing Security AI Workbench is with a new offering, VirusTotal Code Insight, that uses the technology to analyze potentially malicious scripts and explain their behavior, ultimately helping to improve the detection of which scripts are a real threat, Google Cloud said. The offering is now in preview. Other offerings using Security AI Workbench “will be available in preview more broadly this summer,” the company said in a post.

Accenture Managed XDR
Accenture announced at RSAC 2023 that it’s expanding its partnership with Google Cloud around cybersecurity, with the launch of new Managed Extended Detection and Response (XDR) service powered in part by Google Cloud’s new Security AI Workbench offering. The service is built on the cloud-native security information and event management (SIEM) platform from Google Cloud, Chronicle Security Operations, and leverages threat intelligence from Mandiant. The Security AI Workbench provides Accenture’s security analysts with improved productivity and faster access to Mandiant threat intelligence, which is embedded in the offering and can be leveraged through the generative AI interface, according to the companies.
As an example, the system might enable an analyst to more quickly determine — in part through using the embedded threat intelligence — that certain findings in an environment appears to represent a novel pattern of activity, Google Cloud’s Potti told CRN. The use of the technology should enable Accenture’s Managed XDR service to be faster and more effective at catching threats on behalf of customers, Accenture and Google Cloud said.

Cisco XDR
Cisco announced at RSAC that it’s launching a new extended detection and response (XDR) platform that’s been built from the “ground up,” and goes beyond the prior XDR capabilities that have been available in the tech giant’s SecureX offering. The new Cisco XDR platform fuses network detection and response (NDR) and endpoint detection and response (EDR), providing “cross-domain telemetry” in a way that no one else in the market is doing, said Jeetu Patel, executive vice president and general manager of security and collaboration at Cisco. The offering also stands out from security information and event management (SIEM) products by being “near real-time” when it comes to delivering threat detection and prioritization, Patel (pictured) said.
Additionally, Cisco XDR is differentiated by providing “high-fidelity data” from across the company’s various first-party security tools, such as Cisco Secure Client (formerly AnyConnect) for endpoint, he said. The XDR platform integrates a significant number of major third-party security products, as well. Those include EDR tools (Microsoft Defender, Cybereason, Palo Alto Networks Cortex XDR, SentinelOne Singularity and Trend Micro Vision One); email security (Microsoft Defender for Office, Proofpoint); next-Generation firewall from Palo Alto Networks; SIEM from Microsoft Sentinel; and NDR from ExtraHop Reveal(x).
Ultimately, “this one is one of the biggest security product launches we’ve had in a while,” Patel said and represents a major step on Cisco’s journey to fulfill its Security Cloud vision of providing a comprehensive, unified platform for modern security.

IBM Security QRadar Suite
IBM used RSAC to launch a new product suite for security analysts, the IBM Security QRadar Suite. The suite is delivered via SaaS and includes re-architected threat detection and response offerings to improve the speed and efficiency for security teams, IBM said.
Main design upgrades include a unified analyst experience, simplified deployment through SaaS delivery and more than 900 integrations with third-party tools, according to IBM. Key capabilities include AI-powered features such as AI-driven alert triage, automated threat investigation and faster threat hunting, the company said.
The core products making up the new IBM Security QRadar Suite are QRadar Log Insights for cloud-native log management and security observability; QRadar EDR and XDR; QRadar SOAR; and QRadar SIEM. The The QRadar Suite is ultimately “the culmination of years of IBM investment, acquisitions and innovations in threat detection and response,” IBM said in a news release.

CrowdStrike CrowdStream
CrowdStrike and observability startup Cribl announced a new offering at RSAC 2023 that aims to make it easier to get security and IT data onto the CrowdStrike Falcon platform. The new offering, CrowdStream, is powered by the open observability platform from Cribl, a venture-backed company whose investors include CrowdStrike.
The CrowdStream platform natively connects “any data source” to CrowdStrike Falcon using the Cribl observability pipeline, simplifying and lowering the cost of bringing data onto the Falcon platform, the companies said in a news release. The offering ultimately can accelerate adoption of CrowdStrike’s extended detection and response (XDR) and log management technologies, while also helping to aggregate data for the training of AI and machine learning models, according to the companies.

Zimperium Mobile-First Security Platform
Mobile security firm Zimperium announced at RSAC 2023 that it has brought together its capabilities for protecting mobile devices and applications into a single unified offering. Zimperium’s Mobile-First Security Platform combines the vendor’s Mobile Threat Defense product (formerly zIPS) with its Mobile Application Protection Suite, which provides major advantages for security teams and is ultimately the first “end-to-end” platform in mobile security covering both apps and devices, CEO Shridhar Mittal (pictured) said in a news release.
Advantages of unifying the products into a single platform include enabling a centralized interface for accessing and managing both security products, Zimperium said. Other key capabilities of the company’s mobile security products include on-device threat detection — which doesn’t require transferring data to the cloud and back — as well as in-app protection that secures cryptographic keys and blocks reverse engineering, the company said.

Flashpoint Ignite
At RSAC 2023, Flashpoint announced a new intelligence platform, Ignite, aimed at helping organizations to better protect against both cyber and physical threats. The platform stands out by offering intelligence that can serve as a “bridge between teams,” through offering relevant intelligence across multiple different teams within an organization, Flashpoint Chief Product and Engineering Officer Patrick Gardner (pictured) said in a news release.
Key capabilities include Flashpoint Cyber Threat Intelligence, which provides the ability to search thousands of intelligence sources while also monitoring communications between threat actors and gaining access to intelligence reports from Flashpoint analysts, as well. Other major capabilities are vulnerability management, which provides intelligence to help teams with prioritizing and remediating vulnerabilities; Flashpoint Physical Security Intelligence for monitoring and alerting about physical security threats; and Flashpoint National Security Intelligence for “mission-driven teams in Defense, the Intelligence Community, Law Enforcement and Public Safety, State and Local Government, and Federal Civilian Agencies,” the company said in the news release.

Cybersixgill Attack Surface Management
Cyber threat intelligence provider Cybersixgill announced at RSAC that it’s debuting a new attack surface management offering to help security teams prioritize and respond to threats more quickly. The new module utilizes the company’s threat intelligence to eliminate “visibility blindspots” and provide continuous mapping and classification of unknown assets, Cybersixgill said in a news release. This continuous external asset discovery includes identification of domains and subdomains, IPs and hosts, known vulnerabilities, software and certificates, the company said.
Other key capabilities include asset inventory management — with insights into asset association, location and asset type, as well as associated vulnerabilities — and threat intelligence-related asset monitoring to provide an immediate view into potential exposures and related alerts, according to the company.

Torq Hyperautomation Platform
At RSAC 2023, Torq, a startup whose technology offers a no-code method for automating security operations, announced its new Torq Hyperautomation Platform that promises to automate “the most complex security infrastructures at dramatic scale,” the company said in a news release. The startup said that the new platform can bring automation to entire processes and workflows across all of an organization’s security efforts, Torq said.
Key capabilities include the ability to connect all apps and stacks across all infrastructure environments, including Slack, Zoom and Microsoft Teams; support for any command-line interface or programming language to enable “bring your own code”; and orchestration of containerized actions — supporting Docker, Kubernetes, AWS and Azure — to enable “bring your own container.”
Additionally, the Torq Hyperautomation Platform features generative AI capabilities by integrating OpenAI technology, via the ChatGPT API, the company told CRN. The platform can provide answers to questions from users as a way to accelerate resolution of security issues, through a chatbot interface in Slack, Teams, Discord and Zoom, according to Torq.