6 Cool New Zero Trust Security Tools At RSA Conference 2021
Here‘s a look at six new zero trust security offerings at RSA Conference 2021 that make it easier to detect anomalous behavior, ensure credentials aren’t exposed, and spot data exfiltration attempts from cloud services.

Trust No One
See the latest entry: 20 Hottest Cybersecurity Products at RSAC 2022
Vendors attending RSA Conference 2021 have invested heavily in making it easier for customers and partners to apply the principles of least privileged access, verify explicitly, and assume breach. The zero trust security tools leverage conditional access to give administrators more granular access controls and shorten the time needed to detect and resolve incidents.
The offerings ensure credentials aren’t left out in the open and eliminates the risk of theft by restricting data sharing privileges. They also seek to detect anomalous behavior to reduce the risk of insider threat and provide additional context while threat hunting.
From a cloud perspective, the offerings build consistent policy enforcement across all workloads, control access to public apps like Office 365 or Salesforce, and detect data exfiltration attempts from cloud services. Here’s a look at how six zero trust security tools being showcased at RSA Conference 2021 are cutting complexity, reducing cyber-risk and improving performance.

CrowdStrike Zero Trust
CrowdStrike Zero Trust gives organizations visibility into workforce identity across multi-directory, multi-cloud environments. It reduces dynamic friction and false positives by providing conditional access, which shortens the time to detect and resolve incidents by eliminating the need for complex, error-prone log analysis.
This in turn cuts down on alert fatigue, stops attack proliferation, and ensures that security teams are better informed. CrowdStrike Zero Trust reduces the load on security operations center (SOC) analysts with high-fidelity correlations and enhances user experience with adaptive conditional access.
CrowdStrike Zero Trust assesses endpoint security posture and enforces conditional access to resources from compliant endpoints by sharing assessment scores with ecosystem partners. It also ensures consistent login experience for genuine users while enforcing intelligent conditional access to resources and applications only when the risk increases.

Ericom Software ZTEdge
Ericom Software’s ZTEdge is a comprehensive Zero Trust security platform that meets the unique requirements of midsize enterprises and small businesses. It cuts complexity, reduces cyber-risk and improves performance at a dramatically lower price point than alternative solutions, Ericom Software said.
ZTEdge connects the right people and devices to the right applications and resources, and protects users and their devices as they interact with the web and email. It also eliminates credential theft risks and restricts data sharing privileges by controlling access to public cloud apps like Office 365 or Salesforce.
Ransomware spread is stopped and intrusions are detected, blocked and remediated with ZTEdge through network segmentation and monitoring, according to Ericom Software. ZTEdge can be used to connect remote workers to either private cloud or on-premises applications, and also enables local internet breakouts to eliminate traffic backhauling and improve performance.
IBM Security Zero Trust Blueprints
The IBM Security zero trust blueprints offer a framework for building a security program that applies the principles of least privilege access, never trust, always verify, and assume breach. These blueprints can offer companies a prescriptive roadmap of security capabilities along with guidance on how to integrate them as part of a zero-trust approach.
The preserve customer privacy blueprint helps organizations enforce limited and conditional access to all data, give insights into data usage and privacy risk, and reduce exposure in the event of compromise. With the hybrid workforce blueprint, IBM said organizations can build a workforce that can securely connect to any application on any network, from any location using any device.
The insider threat blueprint is designed to detect user behavior anomalies, adaptively enforce security policies with automation, insulate an organization’s most valuable data, and limit business disruption. And with the hybrid cloud blueprint, firms can enable continuous compliance, reporting and response, monitor for cloud misconfigurations, and build consistent policy enforcement across all cloud workloads.
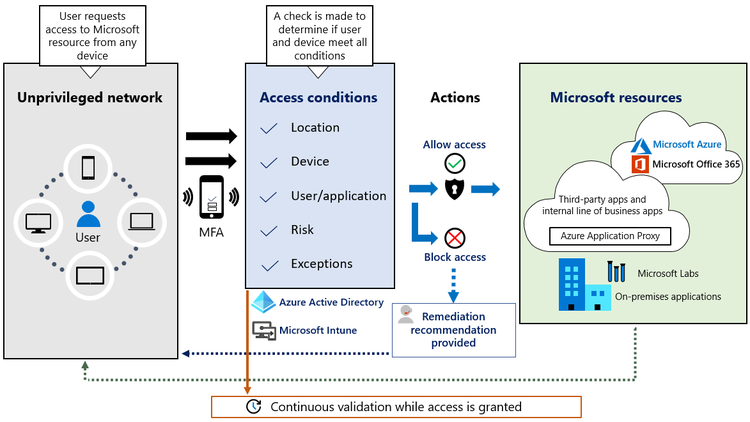
Microsoft Zero Trust Enhancements
Microsoft has rolled out an array of new features that help customers verify explicitly, grant least privileged access, and assume breach. The company rolled out new features for its Azure Active Directory Conditional Access cloud identity offering that give admins more granular access controls while making it easier to control a growing list of policies.
For least privileged access, Microsoft’s debuted the ability to discover and secure unmanaged endpoints and network devices to Microsoft Defender for Endpoint. And Microsoft’s threat and vulnerability management capabilities now also support Linux OS, giving organizations the ability to view discovered vulnerabilities, assess the latest security recommendations, and issue remediation tasks.
Microsoft also rolled out new anomaly detection capabilities – such as User and Entity Behavior Analysis (UEBA) for Azure Sentinel – that can be used to provide additional context while hunting or fused with incidents. And new enhancements to Microsoft Cloud App Security will help protect against attacks by detecting suspicious app activity and data exfiltration attempts from cloud services.

BlackBerry Gateway
BlackBerry Gateway marks the company’s entry into Zero Trust Network Access (ZTNA) for both SaaS and on-premises applications. It helps organizations reduce network access risk by assuming every user, endpoint, and network is potentially hostile until identity is authenticated. The product will be available this month.
Gateway ensures business networks are only accessed by trusted and healthy devices, and provides ZTNA telemetry data that will be added to BlackBerry’s cloud data lake. BlackBerry Gateway can also be integrated with the company’s endpoint security products to provide a comprehensive defense against threats targeting devices, networks, and user identity.

One Identity Starling CertAccess
One Identity Starling CertAccess is an access request and access certification offering that helps organizations leverage Active Directory and Azure Active Directory in the enterprise. It addresses the difficult of managing, securing, and controlling user accounts in Active Directory and Azure Active Directory, both of which introduce opportunities for enterprises to mismanage access.
By enabling employees to request access easily and consistently and for the line of business to certify that access, Starling CertAccess ensures users have the right level of access without leaving credentials vulnerable. Starling CertAccess augments the user and group administrative power of Active Roles and Active Roles On Demand for streamline critical hybrid Azure Directory identity governance tasks.
Advertisement